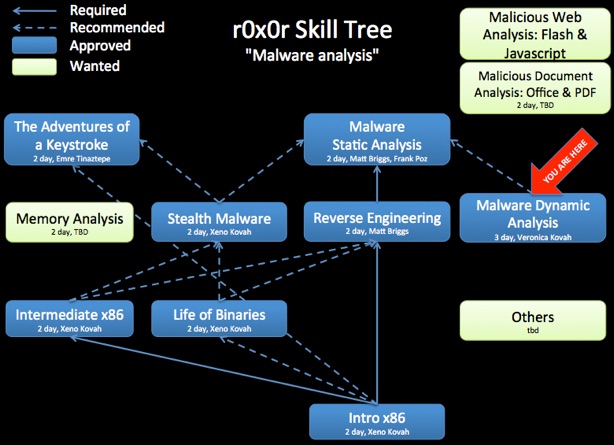
Malware Dynamic Analysis
Creator: Veronica Kovah
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
Class Prerequisites: None
Lab Requirements: Linux system with VirtualBox and Windows XP VM.
Class Textbooks: “Practical Malware Analysis” by Michael Sikorski and Andrew Honig
Recommended Class Duration: 3 days
Creator Available to Teach In-Person Classes: Yes
Author Comments:
This introductory malware dynamic analysis class is dedicated to people who are starting to work on malware analysis or who want to know what kinds of artifacts left by malware can be detected via various tools. The class will be a hands-on class where students can use various tools to look for how malware is: Persisting, Communicating, and Hiding
We will achieve the items above by first learning the individual techniques sandboxes utilize. We will show how to capture and record registry, file, network, mutex, API, installation, hooking and other activity undertaken by the malware. We will create fake network responses to deceive malware so that it shows more behavior. We will also talk about how using MITRE's Malware Attribute Enumeration & Characterization (MAEC - pronounced "Mike") standard can help normalize the data obtained manually or from sandboxes, and improve junior malware analysts' reports. The class will additionally discuss how to take malware attributes and turn them into useful detection signatures such as Snort network IDS rules, or YARA signatures.
Dynamic analysis should always be an analyst's first approach to discovering malware functionality. But this class will show the instances where dynamic analysis cannot achieve complete analysis, due to malware tricks for instance. So in this class you will learn when you will need to use static analysis, as offered in follow the follow on Introduction to Reverse Engineering and Reverse Engineering Malware classes.
During the course students will complete many hands on exercises.
Course Objectives:
* Understand how to set up a protected dynamic malware analysis environment
* Get hands on experience with various malware behavior monitoring tools
* Learn the set of malware artifacts an analyst should gather from an analysis
* Learn how to trick malware into exhibiting behaviors that only occur under special conditions
* Create actionable detection signatures from malware indicators
This class is recommended for a later class on malware static analysis. This is so that students understand both techniques, and utilize the technique which gives the quickest answer to a given question.
Every attempt was made to properly cite references, but if any are missing, please contact the author.

Latest Class Materials
(In the latest slides, the background material is interleaved into the material.)

Class Materials (that match videos)

Day 1 Part 1 : Introduction (8:10)
Day 1 Part 2 : Background: VirtualBox (5:56)
Day 1 Part 3 : Background: PE files & Packers (17:00)
Day 1 Part 4 : Background: File Identification (15:44)
Day 1 Part 5 : Background: Windows Libraries (4:27)
Day 1 Part 6 : Background: Windows Processes (35:16)
Day 1 Part 7 : Background: Windows Registry (18:07)
Day 1 Part 8 : Background: Windows Services (25:52)
Day 1 Part 9 : Background: Networking Refresher (27:38)
Day 1 Part 10 : Isolated Malware Lab Setup (26:47)
Day 1 Part 11 : Malware Terminology (6:50)
Day 1 Part 12 : Playing with Malware: Poison Ivy RAT (30:54)
Day 1 Part 13 : Behavioral Analysis Overview (5:30)
Day 1 Part 14 : Persistence Overview (9:06)
Day 1 Part 15 : Persistence Lab: Using Autoruns.exe to View Persistence (6:54)
Day 1 Part 16 : Persistence Lab: Viewing “Image File Execution Options” registry (6:40)
Day 1 Part 17 : Persistence Lab: Viewing Filesystem Persistence (3:06)
Day 1 Part 18 : Persistence Lab: Using Autoruns to Analyze IMworm’s Persistence (9:07)
Day 2 Part 1 : Day 1 Review (3:16)
Day 2 Part 2 : Persistence Lab: Using Regshot to Analyze IMworm’s Persistence (8:00)
Day 2 Part 3 : Persistence Lab: Using Autoruns to Analyze Hydraq’s Persistence (10:19)
Day 2 Part 4 : Persistence Lab: Using Regshot to Analyze Hydraq’s Persistence (10:49)
Day 2 Part 5 : Maneuvering Overview (2:30)
Day 2 Part 6 : Maneuvering: Code Injection Overview (11:46)
Day 2 Part 7 : Maneuvering: Lab: Using Regshot to analyze Parite (10:06)
Day 2 Part 8 : Background: Windows APIs (21:42)
Day 2 Part 9 : Maneuvering: Lab: Using WinAPIOverride to analyze Onlinegames 1 (30:51)
Day 2 Part 10 : Maneuvering: Lab: Using WinAPIOverride to analyze Onlinegames 2 (21:05)
Day 2 Part 11 : Maneuvering: DLL Search Path Hijacking & Asynchronous Procedure Call (APC) Overview (8:19)
Day 2 Part 12 : Maneuvering: Lab: Checking “Known_Dlls” (3:17)
Day 2 Part 13 : Maneuvering: Lab: Using ProcessMonitor to Analyze Nitol (18:23)
Day 2 Part 14 : Maneuvering: IAT/EAT/Inline Hooking Overview (13:33)
Day 2 Part 15 : Malware Functionality Overview (1:55)
Day 2 Part 16 : Malware Functionality: Keylogging Overview (3:05)
Day 2 Part 17 : Malware Functionality: Analyzing Magania’s Use of SetWindowsHookEx with Rohitab API Monitor (17:33)
Day 2 Part 18 : Malware Functionality: Backdoors Overview (2:56)
Day 2 Part 19 : Malware Functionality: Backdoors Lab: StickyKeys (1:08)
Day 2 Part 20 : Malware Functionality: Phone Home / Beaconing: Lab: Using INetSim to Capture DarkShell’s Beaconing (15:16)
Day 3 Part 1 : Day 2 Review (2:48)
Day 3 Part 2 : Degrading Security (1:19)
Day 3 Part 3 : Degrading Security: Lab: SpyEye (9:54)
Day 3 Part 4 : Degrading Security: Lab: Conficker Prelude (4:39)
Day 3 Part 5 : Analyzing DLLs (13:52)
Day 3 Part 6 : Degrading Security: Lab: Conficker and Service State Diffing (15:03)
Day 3 Part 7 : Self Destruction (22:17)
Day 3 Part 8 : Self-Destruction: Lab: Detection With CaptureBAT (8:18)
Day 3 Part 9 : Hiding Files: Lab: IMWorm (19:09)
Day 3 Part 10 : Self-Avoidance (1:35)
Day 3 Part 11 : Self-Avoidance: Lab: Poison Ivy (8:40)
Day 3 Part 12 : Anti-VM Techniques (1:20)
Day 3 Part 13 : Automated Dynamic Analysis Sandboxes (3:29)
Day 3 Part 14 : Automated Dynamic Analysis Sandboxes: Cuckoo Sandbox: Lab: Poison Ivy (25:13)
Day 3 Part 15 : MAEC (8:25)
Day 3 Part 16 : Automated Dynamic Analysis Sandboxes: Cuckoo Sandbox: Lab: Parite (11:56)
Day 3 Part 17 : Actionable Output: Yara (3:56)
Day 3 Part 18 : Actionable Output: Yara: Lab: Bot Classification (8:16)
Day 3 Part 19 : Actionable Output: Snort (5:21)
Day 3 Part 20 : Actionable Output: Snort: Lab: Detecting Beaconing (8:19)
Day 3 Part 21 : Class Summary (8:30)

Revision History:
10-04-2015 - Uploaded day 3 videos
09-18-2014 - Material updated (25 new slides, background material interleaved rather than all up front), moved from LibreOffice to PowerPoint format due to continued errors with LibreOffice.
08-24-2014 - Day 2 videos added, and Day 1 part 14 broken up into finer-grain videos
08-17-2014 - Day 1 videos added, and updated slides that match videos added
03-17-2013 - Added fine-granularity class map
02-27-2013 - Initial class content upload
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.