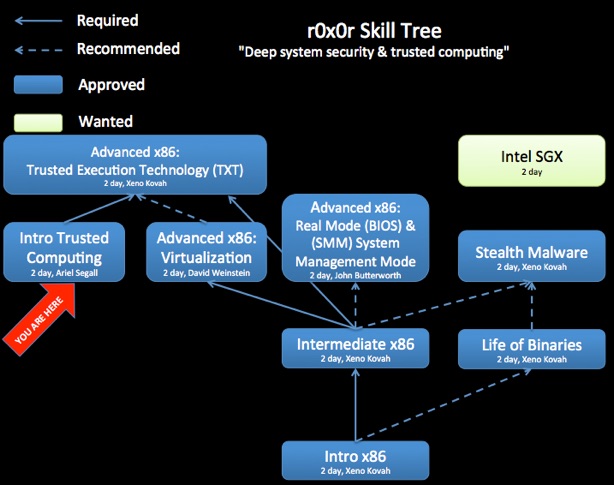
Introduction To
Trusted Computing
Introduction To
Trusted Computing
Creators: Ariel Segall
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
Class Prerequisites: None
Lab Requirements: None
Class Textbook (Optional): “A Practical Guide to Trusted Computing” by David Challener, Kent Yoder, Ryan Catherman, David Safford, and Leendert Van Doorn
Recommended Class Duration: 2 days
Creators Available to Teach In-Person Classes: Yes
Author Comments:
This course is an introduction to the fundamental technologies behind Trusted Computing. You will learn what Trusted Platform Modules (TPMs) are and what capabilities they can provide both at an in-depth technical level and in an enterprise context. You will also learn about how other technologies such as the Dynamic Root of Trust for Measurement (DRTM) and virtualization can both take advantage of TPMs and be used to enhance the TPM's capabilities.
We will cover major use cases for trusted computing, including machine authentication, data protection, and attestation. This course will also introduce you to the various software resources that exist today to support TPMs, give a high-level overview of related research and development projects, and briefly discuss other trusted computing standards such as Trusted Network Connect which may be relevant to enterprise deployment of TPMs and trusted computing.
Objectives:
• Introduce students to both basic and advanced TPM capabilities, as well as other trusted computing standards and technologies
• Show how TPMs and related technologies can be used in enterprise environments and for cutting-edge research
• Give students the necessary tools and information to design and build systems that take advantage of trusted computing

Class Materials

Day 1 Part 1 (19:11, 230 MB) - Introduction
Day 1 Part 2 (15:17, 208 MB) - What is Trusted Computing?
Day 1 Part 3 (61:23, 775 MB) - Introduction to Trusted Computing - TPM 101
Day 1 Part 4 (12:05, 177 MB) - What are TPMs Good (and Not Good) For?
Day 1 Part 5 (11:50, 180 MB) - TPM Myths
Day 1 Part 6 (17:03, 197 MB) - Why Should Enterprises Care About TPMs?
Day 1 Part 7 (24:52, 312 MB) - Beyond the TPM: Roots of Trust for Measurement
Day 1 Part 8 (11:18, 185 MB) - Beyond the TPM: Trusted Network Connect
Day 1 Part 9 (9:20, 154 MB) - Beyond the TPM: Other Technologies
Day 1 Part 10 (4:02, 63 MB) - What Do We Mean by TPM Provisioning?
Day 1 Part 11 (4:33, 69 MB) - TPM Provisioning: Turning on the TPM
Day 1 Part 12 (8:09, 125 MB) - TPM Provisioning: Endorsement Key(EK): Theory vs. Reality
Day 1 Part 13 (21:34, 279 MB) - TPM Provisioning: Creating the EK & Taking Ownership
Day 1 Part 14 (10:27, 158 MB) - TPM Provisioning: Creating Other Keys
Day 1 Part 15 (10:22, 152 MB) - TPM Provisioning: Certifying EK and Other Keys
Day 1 Part 16 (13:09, 188 MB) - Exact Mechanics of TPM Keys: Creating Keys
Day 1 Part 17 (23:00, 302 MB) - Exact Mechanics of TPM Keys: Certifying Keys
Day 1 Part 18 (12:54, 179 MB) - Exact Mechanics of TPM Keys: Using Keys
Day 1 Part 19 (10:32, 115 MB) - End of Day Questions & Answers
Day 2 Part 1 (25:38, 320 MB) - TPM Platform Control Registers (PCRs) & Locality
Day 2 Part 2 (38:21, 456 MB) - Attestation, Quotes, Sealing, & Binding
Day 2 Part 3 (32:01, 372 MB) - Machine Authentication
Day 2 Part 4 (29:06, 346 MB) - Using the TPM for Data Protection & Storage
Day 2 Part 5 (30:56, 381 MB) - Other TPM Features
Day 2 Part 6 (1:01:02, 789 MB) - Navigating the TPM Manuals
Day 2 Part 7 (50:21, 789 MB) - Programming the TPM
(9:28:18 total)

Revision History:
01-19-2013 - Day 2 & Archive.org videos uploaded
01-13-2013 - Day 1 videos uploaded
10-24-2012 - Initial class content upload
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.