Advanced x86:
Introduction to BIOS & SMM
Advanced x86:
Introduction to BIOS & SMM
YOU SHOULD BE WATCHING THE UPDATED OST2 VERSION INSTEAD OF THIS!
Creator: (2014) John Butterworth @jwbutterworth3
Instructor: (2014) John Butterworth
(2014-current) Xeno Kovah @xenokovah
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
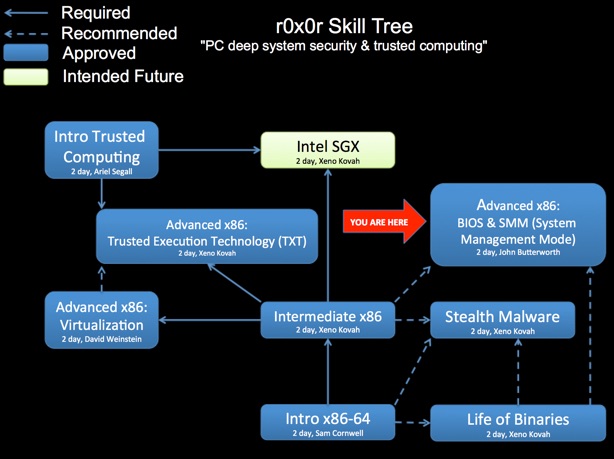
Class Prerequisites: While it is possible to do OK in this class without this background knowledge, ideally you should have taken Intro x86 (for knowledge of assembly), Introduction to Reverse Engineering Software (for knowledge of reversing, for application to BIOS), Intermediate x86 (for knowledge of GDT, and port IO), and Life of Binaries (for knowledge of the PE format), or equivalent knowledge.
Lab Requirements: Windows >= 7
Class Textbooks: None
Recommended Class Duration: 2-3 days
Instructor Available to Teach In-Person Classes: Yes
Author Comments:
PC BIOS/UEFI firmware is usually “out of sight, out of mind”. But this just means it’s a place where sophisticated attackers can live unseen and unfettered. This class shares information about PC firmware security that was hard-won over years of focused research into firmware vulnerabilities.
We will cover why the BIOS is critical to the security of the platform. This course will also show you what capabilities and opportunities are provided to an attacker when BIOSes are not properly secured. We will also provide you tools for performing vulnerability analysis on firmware, as well as firmware forensics. This class will take people with existing reverse engineering skills and teach them to analyze UEFI firmware. This can be used either for vulnerability hunting, or to analyze suspected implants found in a BIOS, without having to rely on anyone else.
Learning Objectives
* Understand the similarities and differences between the UEFI and legacy BIOS
* Understand the BIOS/UEFI boot environments and how they interact with the platform architecture
* How the BIOS/UEFI should configure the system to maximize platform security, and how attackers have bypassed these security mechanisms
* How System Management Mode (SMM) is instantiated and must be protected
* How SMM may be used to provide added layers of platform security
* How the BIOS flash chip should be locked down, and what kind of attacks can be done when it is not
* Learn how to Reverse Engineer UEFI modules
* To teach you “how to fish” so you can take your newly-acquired knowledge to perform further security research in this area

Latest Class Materials (Xeno Kovah - 10-14-2015)
Day 1
Day 2

Original Public Released Class Materials (John Butterworth - 2014)

Revision History:
10-14-2015 - Initial class content (John’s version & Xeno’s version) uploaded
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.