Android Forensics &
Security Testing
Android Forensics &
Security Testing
Creator: Shawn Valle
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
Class Prerequisites: Basic knowledge of the Android OS.
Lab requirements:
1. VMWare Player or Workstation, configured for NAT
2. Android SDK for Windows installed
http://dl.google.com/android/installer_r16-windows.exe
3. QtADB for Windows downloaded and extracted:
http://motyczko.pl/qtadb/QtADB_0.8.1_windows.zip
4. SuperOneClick for Windows: http://depositfiles.com/files/n0dcxce3t
5. Audio/video for video demonstrations
6. Custom Ubuntu virtual machine requires 20GB available space on each
workstation, alternatively Santoku Linux available from http://viaforensics.com
Class Textbook: Android Forensics, by Andrew Hoog.
Class Prerequisites: Must have a basic understanding of Windows command line and
Linux/UNIX terminal. Good to have experience with the Android operating
system or development environment.
Recommended class duration: 2 days
Creator Available to Teach In-Person Classes: Yes
Author comments:
This course will cover the most common issues facing mobile devices, and general tips for securing mobile applications. Upon completion of general mobile security overview, the course will delve into a proven practice in Mobile Device Forensics and Mobile Application Penetration Testing for Android devices. Over the two-day course, students will get hands-on time with open-source and commercial forensics tools, setup and explore reverse engineering development environments, and experience the process with which professional mobile security engineers have successfully applied to several projects. Areas covered include, identifying application vulnerabilities, code analysis, memory & file system analysis, and insecure storage of sensitive data.
Course Objectives include:
1. Extract and analyze data from an Android device
2. Manipulate Android file systems and directory structures
3. Understand techniques to bypass passcodes
4. Utilize logical and physical data extraction techniques
5. Reverse engineer Android applications
6. Analyze acquired data
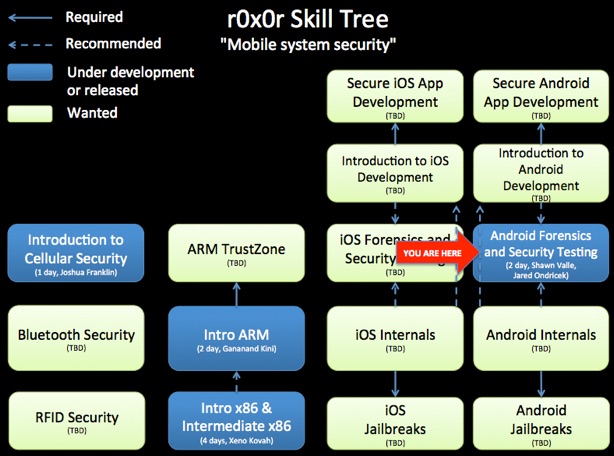
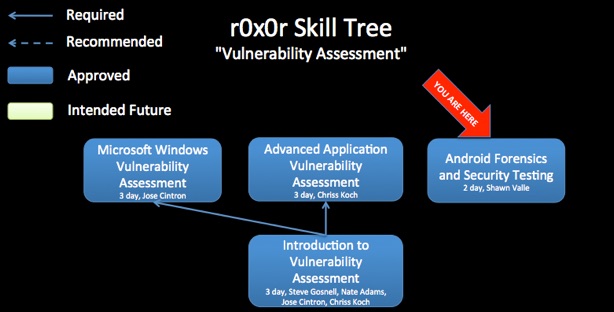
This class serves as a foundation for mobile digital forensics, forensics of Android operating systems, and penetration testing of Android applications. Although delivered in a single offering, the course can be broken into separate offerings. The mobile digital forensics portion could be leveraged and reused for introducing forensics of other mobile platforms.
The instructor-led lab work will include:
* Creating an Android Virtual Device for use during the class
* Identifying file system directories and becoming familiar with the directory tree
* Verifying we can connect an Android device to a forensic workstation
* Attempting to access shell and locate data directories
* Becoming familiar with common command line utilities for locating data
* Exploring most common data directories and databases
* Attempting to circumvent passcodes and obtain temp root access
* Extracting a logical acquisition from device or AVD
* Documenting extracted data
* Exploring different commercial and open-source Android forensics products
* Identifying data on device which can be used as evidence to identify user activity
Due to the nature of the rapidly maturing Android platform and mobile digital forensics, the author is making regular updates to course content. For updated material, or to submit any suggestions, corrections, or changes, please email me at the address included in the slides.


Revision History:
01-07-2013 - Initial class content upload
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.