Intermediate Intel x86: Architecture, Assembly, Applications, & Alliteration
YOU SHOULD BE WATCHING THE UPDATED OST2 VERSION INSTEAD OF THIS!
Creator: Xeno Kovah @XenoKovah
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
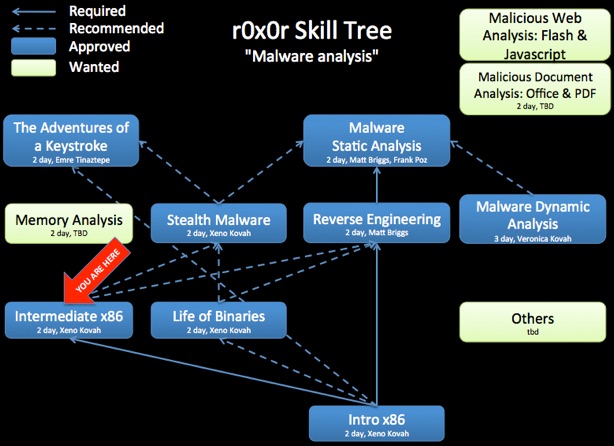
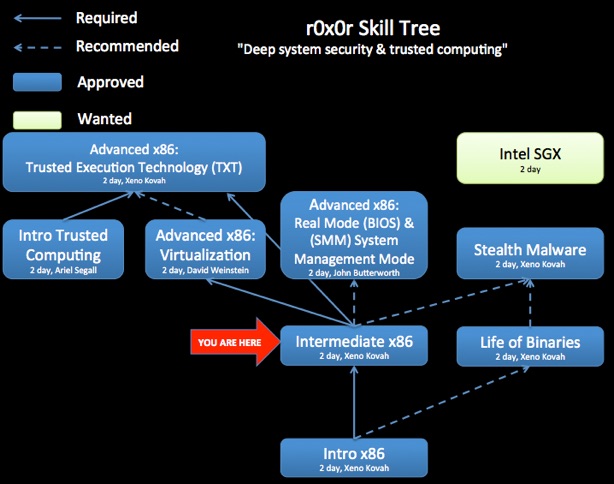
Class Prerequisites: Introduction to x86
Lab Requirements: Requires a Windows system with Visual C++ Express Edition, Windows DDK or WDK kernel compilation environment, and WinDbg. Requires a Windows guest OS running in VMWare Player or VMWare Server in order to do kernel debugging with WinDbg from the host OS.
Class Textbook: None
Recommended Class Duration: 2-3 days
Creator Available to Teach In-Person Classes: Yes
Author Comments:
Building upon the Introductory Intel x86 class, this class goes into more depth on topics already learned, and introduces more advanced topics that dive deeper into how Intel-based systems work.
Topics include, but are not limited to:
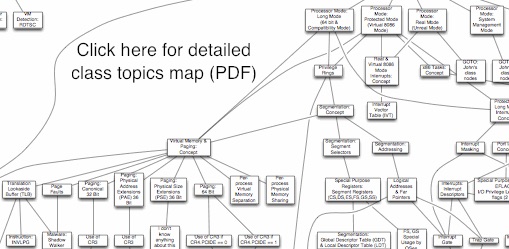
•Physical and virtual memory and how a limited amount of physical memory is represented as much more virtual memory through a multilevel paging system. We will also talk about memory segmentation.
•The hardware basis for kernel versus userspace separation and how software transitions between the two. This portion answers the question of why does x86 have 4 “rings”, with ring 0 being the most privileged, and ring 3 being the least.
•Hardware and software interrupts, and how they are the basis for debugging.
•Input/Output instructions and how these allow the CPU to talk to peripherals.
Example applications include showing how hardware and memory mechanisms are used for software exploits, anti-debug techniques, rootkit hiding, and direct hardware access for keystroke logging.
This material includes labs on:
•Using WinDbg to perform kernel debugging on a virtual machine (which is equally applicable for debugging a real machine.)
•Using a custom WinDbg plugin to examine the Local (memory segment) Descriptor Table (LDT), and Global (memory segment) Descriptor Table (GDT) in order to understand how Windows sets memory segment ranges and permissions for userspace and kernel space.
•Using WinDbg and the !pte command to understand how Windows organizes its paging structures which map physical memory to virtual memory.
•Investigating where exactly the XD/NX bit is set in order to make memory as non-executable (which Microsoft calls Data Execution Prevention (DEP)), to prevent some types of exploits from succeeding.
•Using the Read Timestamp Counter (RDTSC) instruction to profile code execution time. Also, using a profile of code execution time to change a program’s behavior in the presence of a debugger (e.g. executing different code if the code appears to have been stopped at a breakpoint.)
•Printing information about task state segments, which hold information that is used to find the kernel stack when an interrupt occurs.
•Watching what does and doesn’t change when a software interrupt is used to transfer control from userspace to kernel.
•Reading the Interrupt Descriptor Table (IDT) and understanding the security implications of changes to it.
•Understanding how RedPill uses the IDT in order to detect that a system is virtualized.
•Having a process read its own memory when a software breakpoint is set, in order to see how a debugger will change memory to set the breakpoint but hide the change from the user.
•Watch how hardware-based breakpoints manipulate dedicated debug registers.
•Using port input/output to access the backdoor communications channel that VMWare uses in order to send copy/paste, mouse movement, and other events in and out of a VM.
•Using port I/O in order to talk directly to the PS2 keyboard controller in order to sniff keystrokes or flash keyboard LEDs.
Knowledge of this material is strongly encouraged for future classes such as Rootkits.
A student Q&A forum has been set up at http://www.reddit.com/r/OST_IntermediateX86.
To submit any suggestions, corrections, or explanations of things I didn’t know the reasons for, please email me at the address included in the slides.
This is why it’s good to have a guide ;)
Author Biography: Xeno co-founded LegbaCore in January 2015 to focus on improving firmware security. He is also the founder and lead contributor to OpenSecurityTraining.info. He has posted 9 full days of class material material on x86 assembly, architecture, binary formats (PE and ELF), and Windows rootkits. He has a Bachelors of Science in Computer Science from the University of Minnesota Twin Cities, and an Masters of Science in Information Security Technology and Management from Carnegie Mellon University. He attended CMU through the National Science Foundation Scholarship for Service (aka CyberCorps) program. His specialty area is stealth malware and its ability to hide from security software and force security software to lie. To combat such attacks he researches trusted computing systems that can provide much stronger security guarantees than normal COTS. He has presented at BlackHat USA/EUR, IEEE S&P, ACM CCS, Defcon, CanSecWest, PacSec, Hack in the Box KUL/AMS, Microsoft BlueHat, Shmoocon, Hack.lu, NoSuchCon, SummerCon, ToorCon, DeepSec, VirusBulletin, MIRCon, AusCERT, Trusted Infrastructure Workshop, NIST NICE Workshop, DOD Information Assurance Symposium, and MTEM.

Class Materials

Day 1 Part 1 (44:23, 445 MB)
Day 1 Part 2 (58:25, 631 MB)
Day 1 Part 3 (1:10:50, 760 MB)
Day 1 Part 4 (1:17:25, 1 GB)
Day 1 Part 5 (59:50, 678 MB)
Day 1 Part 6 (1:05:42, 750 MB)
Day 2 Part 1 (1:47:27, 1.3 GB)
Day 2 Part 2 (37:33, 453 MB)
Day 2 Part 3 (1:08:29, 822 MB)
Day 2 Part 4 (56:28, 761 MB)
Day 2 Part 5 (1:15:05, 1 GB)
Day 2 Part 6 (1:03:01, 874 MB)
Day 2 Part 7 (24:02, 341 MB)
(13:28:40 total, sans lab time)
The videos are useful for students, but also more useful for potential instructors who would like to teach this material. By watching the video, you will better understand the intent of some slides which do not stand on their own. You are recommended to watch the largest size video so that the most possible text is visible without having to follow along in the slides.

Revision History:
03-17-2013 - Made fine-grain class map more prominent at bottom of the page
04-22-2012 - Videos uploaded to Youtube
07-15-2011 - Videos uploaded to Archive.org
02-16-2011 - Initial class content upload
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.