Introductory Intel x86: Architecture, Assembly, Applications, & Alliteration
YOU SHOULD BE WATCHING THE UPDATED OST2 VERSION INSTEAD OF THIS!
Creator: Xeno Kovah @XenoKovah
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
Class Prerequisites: Must have a basic understanding of the C programming language, as this class will show how C code corresponds to assembly code.
Lab Requirements: Requires a Windows system with Visual C++ Express Edition. Requires a Linux system with gcc and gdb, and the CMU binary bomb installed (use the one below, that link now holds the 64 bit version and this is the 32 bit class). Either system can be physical or virtual.
Class Textbook: “Professional Assembly Language” by Richard Blum. This was chosen as a reference book because it provides an alternate explanation for all the instructions covered in the class. However it is Linux and AT&T syntax focused rather than Windows and Intel syntax.
Recommended Class Duration: 2-3 days
Creator Available to Teach In-Person Classes: Yes
Author Comments:
Intel processors have been a major force in personal computing for more than 30 years. An understanding of low level computing mechanisms used in Intel chips as taught in this course serves as a foundation upon which to better understand other hardware, as well as many technical specialties such as reverse engineering, compiler design, operating system design, code optimization, and vulnerability exploitation.
25% of the time will be spent bootstrapping knowledge of fully OS-independent aspects of Intel architecture. 50% will be spent learning Windows tools and analysis of simple programs. The final 25% of time will be spent learning Linux tools for analysis.
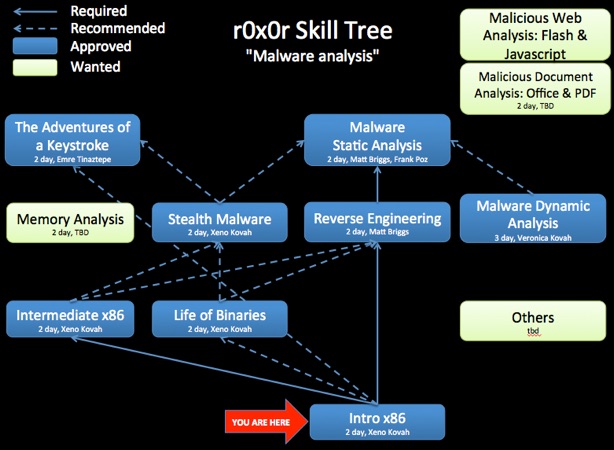
This class serves as a foundation for the follow on Intermediate level x86 class. It teaches the basic concepts and describes the hardware that assembly code deals with. It also goes over many of the most common assembly instructions. Although x86 has hundreds of special purpose instructions, students will be shown it is possible to read most programs by knowing only around 20-30 instructions and their variations.
The instructor-led lab work will include:
* Stepping through a small program and watching the changes to the stack at each instruction (push, pop, call, ret (return), mov)
* Stepping through a slightly more complicated program (adds lea(load effective address), add, sub)
* Understanding the correspondence between C and assembly control transfer mechanisms (e.g. goto in C == jmp in ams)
* Understanding conditional control flow and how loops are translated from C to asm(conditional jumps, jge(jump greater than or equal), jle(jump less than or equal), ja(jump above), cmp (compare), test, etc)
* Boolean logic (and, or, xor, not)
* Logical and Arithmetic bit shift instructions and the cases where each would be used (shl (logical shift left), shr (logical shift right), sal (arithmetic shift left), sar(arithmetic shift right))
* Signed and unsigned multiplication and division
* Special one instruction loops and how C functions like memset or memcpy can be implemented in one instruction plus setup (rep stos (repeat store to string), rep mov (repeat mov)
* Misc instructions like leave and nop (no operation)
* Running examples in the Visual Studio debugger on Windows and the Gnu Debugger (GDB) on Linux
* The famous "binary bomb" lab from the Carnegie Mellon University computer architecture class, which requires the student to do basic reverse engineering to progress through the different phases of the bomb giving the correct input to avoid it “blowing up”. This will be an independent activity.
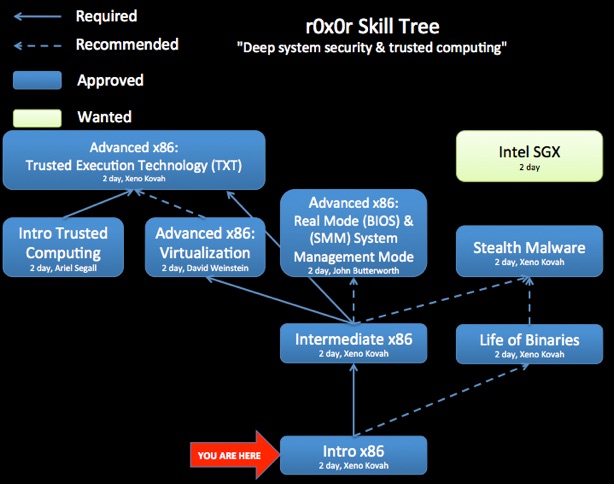
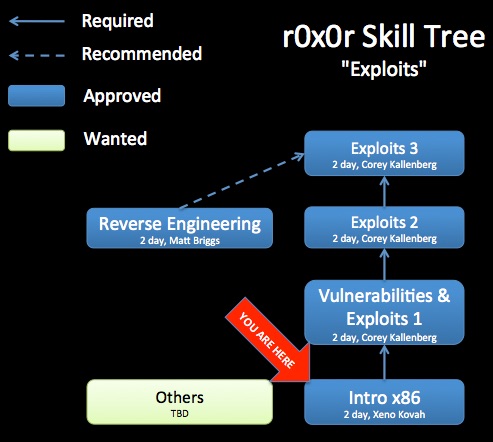
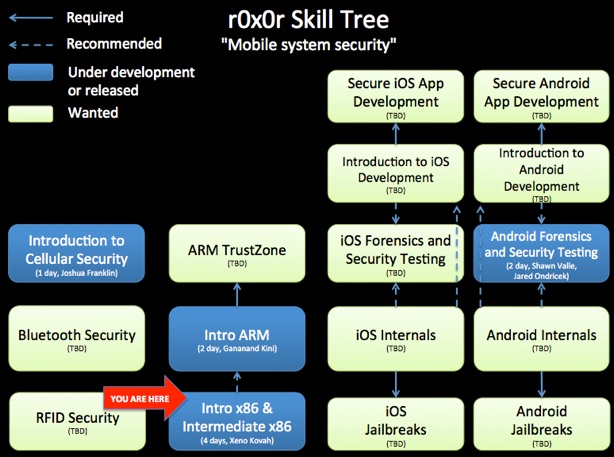
Knowledge of this material is a prerequisite for future classes such as Intermediate x86, Rootkits, Exploits, and Introduction to Reverse Engineering.
Special Thanks to Reza Fatahi for helping create captions for Day 1 Parts 1-2 of the YouTube videos!
A student Q&A forum has been set up at http://www.reddit.com/r/OST_IntroX86.
To submit any suggestions, corrections, or explanations of things I didn’t know the reasons for, please email me at the address above.
Author Biography: Xeno co-founded LegbaCore in January 2015 to focus on improving firmware security. He is also the founder and lead contributor to OpenSecurityTraining.info. He has posted 9 full days of class material material on x86 assembly, architecture, binary formats (PE and ELF), and Windows rootkits. He has a Bachelors of Science in Computer Science from the University of Minnesota Twin Cities, and an Masters of Science in Information Security Technology and Management from Carnegie Mellon University. He attended CMU through the National Science Foundation Scholarship for Service (aka CyberCorps) program. His specialty area is stealth malware and its ability to hide from security software and force security software to lie. To combat such attacks he researches trusted computing systems that can provide much stronger security guarantees than normal COTS. He has presented at BlackHat USA/EUR, IEEE S&P, ACM CCS, Defcon, CanSecWest, PacSec, Hack in the Box KUL/AMS, Microsoft BlueHat, Shmoocon, Hack.lu, NoSuchCon, SummerCon, ToorCon, DeepSec, VirusBulletin, MIRCon, AusCERT, Trusted Infrastructure Workshop, NIST NICE Workshop, DOD Information Assurance Symposium, and MTEM.

Class Materials

Day 1 Part 1 (1:26:50, 789 MB)
Day 1 Part 2 (1:25:05, 993 MB)
Day 1 Part 3 (1:10:04, 872 MB)
Day 1 Part 4 (1:09:26, 673 MB)
Day 1 Part 5 (51:38, 522 MB)
Day 2 Part 1 (1:14:11, 1008 MB)
Day 2 Part 2 (54:53, 844 MB)
Day 2 Part 3 (1:01:08, 795 MB)
Day 2 Part 4 (46:19, 697 MB)
Day 2 Part 5 (58:49, 728 MB)
Day 2 Part 6 (1:10:01, 955 MB)
(12:08:24 total, sans lab time)
The videos are useful for students, but also more useful for potential instructors who would like to teach this material. By watching the video, you will better understand the intent of some slides which do not stand on their own. You are recommended to watch the largest size video so that the most possible text is visible without having to follow along in the slides.

Revision History:
03-17-2013 - Made fine-grain class map more prominent at bottom of the page
07-07-2012 - Uploaded OpenOffice and PDF formatted slides
04-14-2012 - Videos uploaded to YouTube
06-27-2011 - Videos uploaded to archive.org
02-16-2011 - Initial class content upload
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.