The Adventures of a Keystroke:
An in-depth look into keyloggers on Windows
The Adventures of a Keystroke:
An in-depth look into keyloggers on Windows
Creator: Emre TINAZTEPE
License: Creative Commons: Attribution, Share-Alike
(http://creativecommons.org/licenses/by-sa/3.0/)
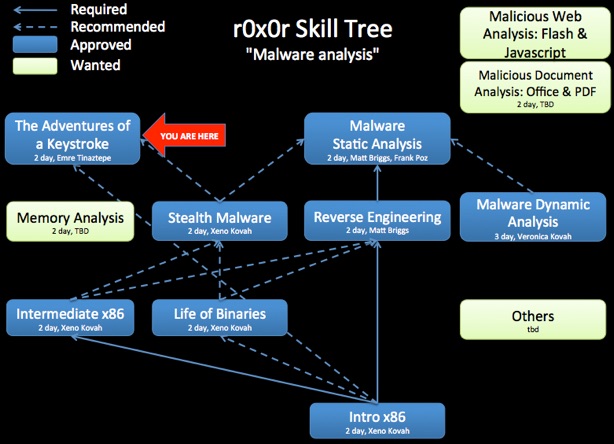
Class Prerequisites: Recommended, but not required, to have taken Introduction to x86.
Lab Requirements: Lab Requirements: Requires two VMs (one for Windows users)
1. Windows 7 x32 as our debuggee,
2. Windows 7 x64 as the debugger.
Class Textbook: Recommended, but not required, is Windows Internals 6th edition, Part 1 and Part 2. This provides a large amount of detail on Windows’ internals, of which keystroke-relevant components are a small part. But the books can provide additional information that people interested in deep system security may be interested in.
Recommended Class Duration: 2 days
Creator Available to Teach In-Person Classes: Yes
Author Comments:
Keyloggers are one of the most widely used components in malware. Keyboard and mouse are the devices nearly all of the PCs are controlled by, this makes them an important target of malware authors. If someone can record your keystrokes then he can control your whole PC without you noticing.
Windows is designed to be compatible with a lot of devices which is why there are a lot of layers in the keystroke handling. The more layers a system has, the more probable it could be compromised by bad guys. There are more than 30 methods for capturing keystrokes from a Windows PC. Methods vary from simple user mode techniques to advanced ones such as IRP hooking.
Class currently covers most of the user mode and kernel mode techniques including the undocumented ones which are not described anywhere else but there are still techniques which are not covered in the class such as Raw Input Devices. As for the hardware, we only cover PS/2 keyboards for the moment but documenting USB keyboards is one of the planned topics for near future.
TODO:
- Add Raw Input Devices
- Add UI Automation
To submit any suggestions, corrections, or explanations of things I didn’t know the reasons for, please email me at the address listed above.
Author Biography: Emre has a BS in Systems Engineering from the Turkish War Academy. Having served as a first lieutenant in many regions including the Iraq, proposing more than 10 military projects and leading small sized teams under very harsh conditions, he has resigned in 2011. He has been programming in a variety of languages till 1998. He is currently leading Zemana Development Team and analyzing malware on a daily basis. He likes to deal with OS Internals and low level stuff.

Class Materials

Revision History:
Oct 14 2014 - Initial class content upload
If you have used and modified this material, we would appreciate it if you submit your modified version for publishing here, so that all versions can benefit from your changes.